The legal profession is one of those where cyber security best practices aren't just desirable; they are essential, given the highly sensitive information accessed on a daily basis.
Here are my top 5 legal professional security tips to help keep you and your firm safe.
1. Secure your equipment
Enable encryption on your device
Device encryption comes in many flavours, but I would say that the two you need to ensure are enabled are TPM and disk encryption.
TPM, or Trusted Platform Module, is a microcontroller which securely stores critical information on your computer. I won’t go into the details of what a microcontroller is; I’ll only say that if you’re on a Windows-based laptop, you should have this enabled. For the most part, and certainly if you’re running Windows 11, this will be enabled by default.
Next is disk encryption. This is the most important thing to have enabled. It works by encrypting information stored on your computer’s SSD, which is the device responsible for storing data. If your SSD is removed from your laptop, the information is completely meaningless without the correct encryption key. This encryption key is typically stored in the TPM, which we summarised in the previous chapter.
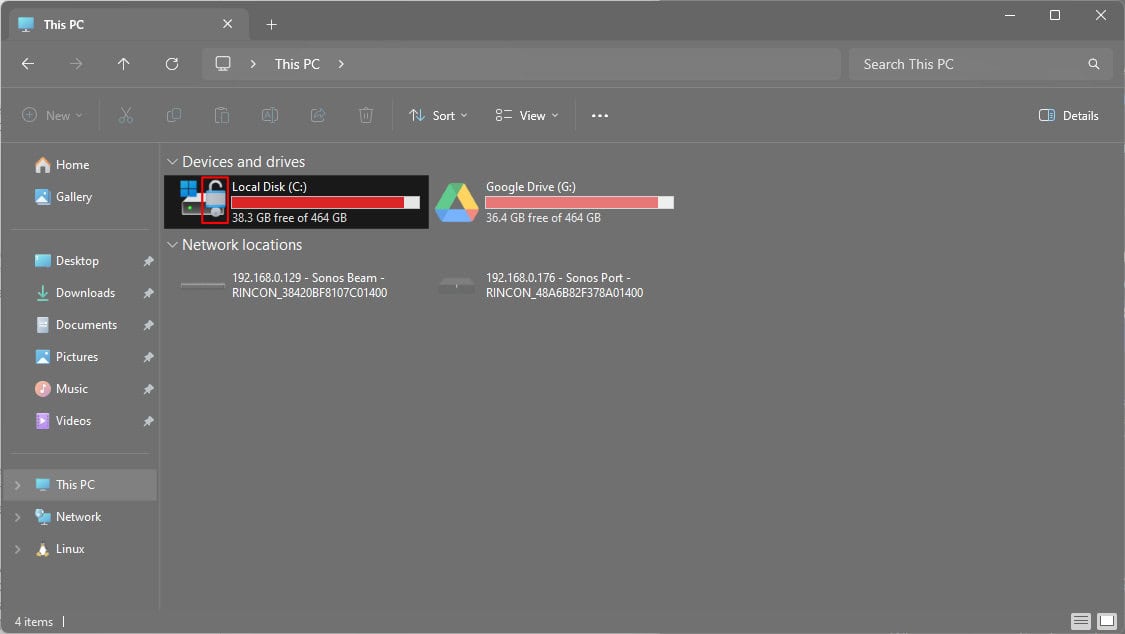
As you can see in the screenshot above, the local storage on my laptop has a padlock over the icon. This means that it has Microsoft’s proprietary encryption enabled. You can find out how to enable this on Microsoft’s website, or speak to your IT department if you don’t have this enabled.
Encrypting USB flash drives
In a cloud-connected world, USB flash drives for moving or storing essential information should be a thing of the past. However, if it’s not, you should always encrypt USB flash drives. Just like with integrated storage, encryption is a straightforward process that ensures the data contained is safe.
By default, encryption is not enabled on USB flash drives, but this can be enabled by right clicking the USB device and selecting ‘Turn BitLocker on’ (In Windows 11 you need to choose ‘Show more options’ if you don’t see this option).
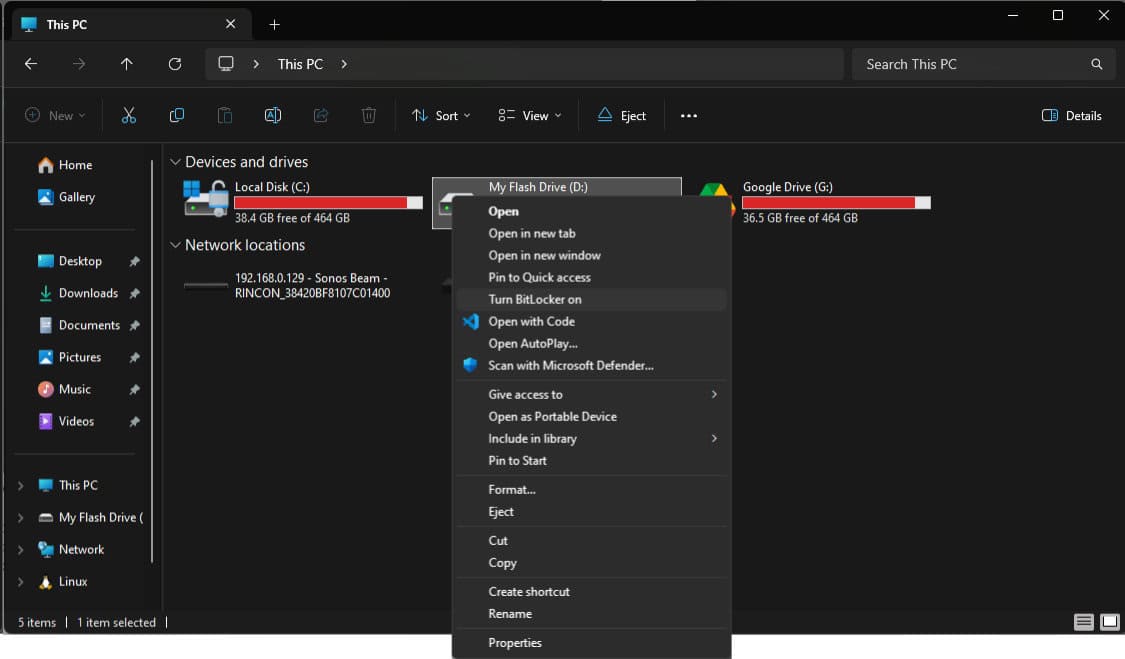
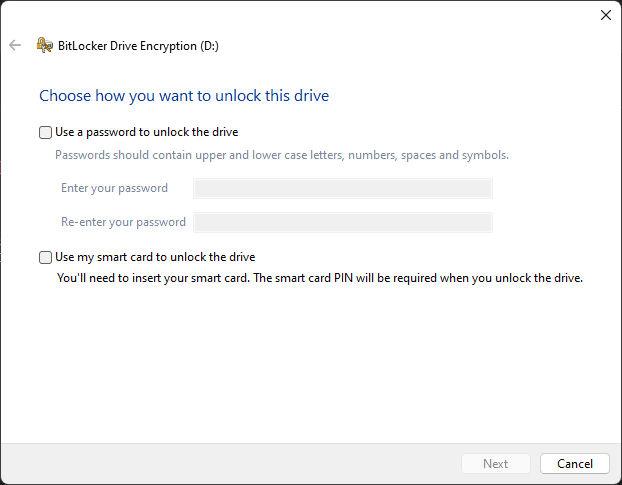
Smart cards are often used to identify yourself on corporate laptops, so if this is the case, choose this option. You will know if this is the case if you need to slot a physical card into your laptop before using it.
That’s it! If you put this USB drive into another computer, the contents won’t be accessible without your smart card or password. Please note that this usually doesn’t work cross-platform, so if you encrypt your USB flash drive on a Windows-based computer, it won’t work on a Mac for example.
2. Don’t get caught out by phishing attacks
We often hear the term “phishing” thrown about, but what is it? As a legal professional, it’s important to understand what a phishing attack is and how to look out for them. While many assume this is one of the legal professional security tips that you don’t need us to tell you, there are still countless people who get caught out on a daily basis.
A phishing attack is where an email or SMS looks like it’s from a legitimate service or business, but has been mimicked by a hacker in order to obtain your information. They often look genuine, ask you to login to a genuine-looking website, but are hosted by hackers to gain your login credentials.
Check who the email is from
An important first step is to see who the email is from. While not completely foolproof, it is a good indicator to see if the origin of the email is legitimate. For example, you might receive an email from Accounts who use Salesforce to say your account has been hacked and you need to login to confirm your details. You check the sender and see ‘[email protected]’. This looks suspicious; it’s not the email address you’d associate with SalesForce. This is an indicator that this is a phishing email.
Luckily, th4ts3cur1ty.company have developed a tool called Dracoeye to check details like these to see if they’re suspicious.
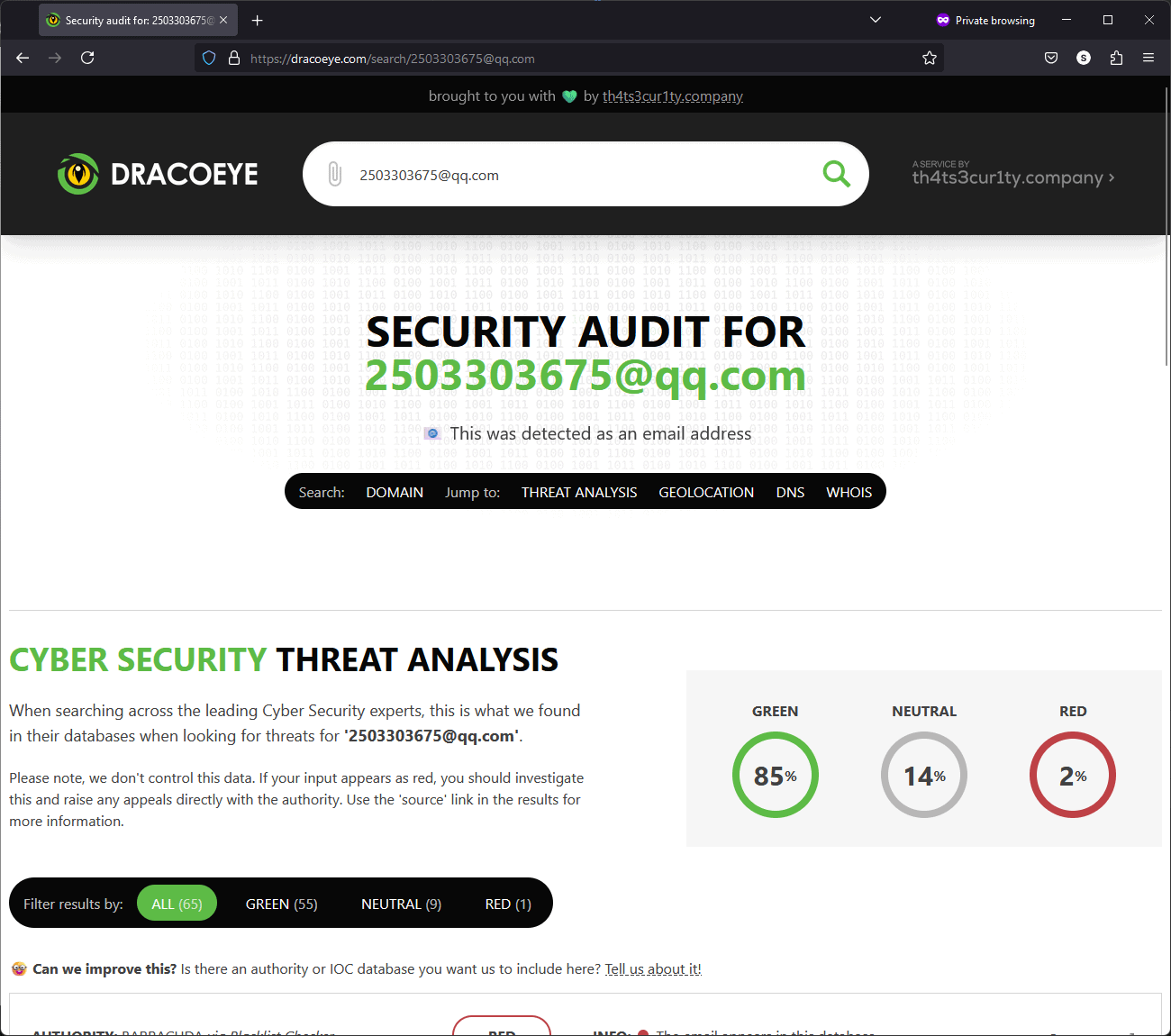
When searching for this particular email address, we can see there’s one red flag, where this email shows as categorically being used in a phishing attack, as well as 9 neutral, where there’s indicators it could be associated with the domain (the bit after the ‘@’ in an email). This will give you peace of mind that this was a phishing attack and shouldn’t be actioned.
Phishing isn’t just limited to services. For instance, you may see an email from a colleague asking to share login details. This should be a red flag in itself, so always call the person or speak to them, or email them on their corporate email address to see if it is genuine. Make sure you do this in a brand-new email to confirm the address, not by replying to the email you received. If it was a genuine request, you should never send credentials over email.
In the legal profession accountability is everything, and you don’t want to be made accountable for someone else’s actions by them using your credentials. If there’s an internal policy in place to raise these requests, especially if you don’t feel comfortable, always do so. Failing that, Password Managers have mechanisms in place to securely provide shared credentials.
Check web links in SMS or emails
As with emails, Dracoeye allows you to check web links in suspicious emails and SMS messages. Just like with checking emails, you can either provide the full link or the domain. Dracoeye will do the rest.
Obviously, relying on tooling alone is not enough, as you may receive false-positives if the particular domain or URL hasn’t yet been caught by the cyber security community. So if it doesn’t look right, or contains extra words you’re not expecting, delete it.
What do I mean by extra words, I hear you ask? Going back to our Salesforce example earlier, if the domain was something like ‘salesforcecybersecurityteam.net’, it’s probably masquerading as being genuine. Typically, genuine businesses wouldn’t use domains like this and instead would either be a sub-domain of their main domain like ‘comms.salesforce.com’ or just ‘salesforce.com’.
3. Stay secure when you’re out and about
The next of our legal professional security tips relates to security outside your home or workplace. As a legal professional, chances are that you often work in public spaces such as cafes, trains or on-premises at a client’s office. There’s a number of ways in which you can ensure cyber security and information security in these scenarios.
Privacy Screen Filters
One of my legal professional security tips which many don’t consider are privacy screen filters; a must-have for public spaces. They’re cheap, simple to install and very effective. They work by being placed over your screen on your laptop or tablet, and mean that only you can see the information displayed on your screen. Anyone looking at your screen over your shoulder or at a slight angle see nothing but black.

These are available pre-cut for most laptops on Amazon or from companies like 3M. To know whether this has been added already, simply look at your screen from an angle; if it goes black, you already have one. If not, speak to your IT department about getting one installed.
Securely use public WiFi with a VPN
Public WiFi is a notorious no-go zone where it comes to cyber security. Bad actors on open WiFi networks can deploy attacks on your laptop, exposing you to data loss or being hacked.
To help combat this, you should always use a trusted VPN on networks that are not known to you; i.e. any WiFi or wired network that is not your home or office. Even at home, you should generally still use your trusted VPN when using your work equipment.
So, you’ll be asking, “what on earth is a trusted VPN?”. Well, let’s start with the VPN part. VPN is a “Virtual Private Network”, and essentially connects you to another network – over which your data is sent – on top of the network you’re connected to. So, for example, if you are in a coffee shop and connected to their open WiFi network, by connecting to a VPN you should no longer be vulnerable to common cyber attacks. This is because the data your laptop is sending and receiving is done over an encrypted connection that the VPN provides, not over the open public network.

The ‘trust’ element comes from it being a VPN that your IT department has provided for company use. If you don’t have a corporate VPN in place, it is essential that you speak to your IT department…and don’t be tempted to use an “off the shelf” service. VPNs vary in level of protection and quality, so it is up to your IT department to ensure this is provided.
VPNs have other advantages, such as providing access to internal resources such as storage, printers and internal tooling.
Always lock your laptop and, where possible, take it with you at all times
An obvious one, but back to basics; keep your laptop with you at all times and don’t leave it somewhere. Obviously, there are exceptions to this – such as being at a client’s office and you needing a toilet break – but your default position should be never to leave it behind.
If you do need to leave it somewhere temporarily, lock it when you leave. In Windows, pressing the ‘Windows Key’ and ‘L’ together will lock it. On a Mac, ‘CTRL + ‘CMD’ + ‘Q’ will lock your screen. On a Chromebook, ‘Search’ + ‘L’ will achieve the same.
If you lose your laptop, always contact your IT department immediately. More often than not, they will have the ability to remotely wipe the device. If you fear the repercussions, it is always better to have lost a laptop and report it, than losing it and potentially exposing the data contained on it. This goes hand-in-hand with my advice on encrypting your laptop’s data.
4. Good password hygiene
Another one of my legal professional security tips which might seem obvious is good password hygiene; easy to get right, but catastrophic when passwords are leaked. Passwords alone are not enough, and secondary security measures such as 2FA (Two-Factor Authentication) should be used in conjunction with strong passwords to keep you and your client data safe.
I’ve recently written an article on Good Password Hygiene, which I’ll summarise here. Ideally, your passwords should always be a minimum of 8 characters long, contain uppercase and lowercase letters, contain symbols such as ‘@%&$ etc’ and numbers. Every single website you use should have its own password too.
Use a Password Manager
Obviously, memorising thousands of passwords is completely unreasonable, so this is where Password Managers come in. They work by generating and securely storing the passwords you use for various services, where you only need to memorise one password to unlock your password vault. From there, the password manager will sort out automatically filling in login screens on websites.
There are many, and some have been hacked. Personally I can only recommend Bitwarden and Keeper, although there are many good alternatives. LastPass has been compromised more than once so my personal opinion is that LastPass should be avoided.
Speak to your IT department about whether they have an authorised Password Manager in place; otherwise, do your research before choosing one.
Use MFA or 2FA
Ahh, another acronym, but an important one! MFA stands for “Multi-Factor Authentication” and 2FA means “Two-Factor Authentication”. Generally, they mean the same thing, but sometimes MFA has more than two steps.
These work by using a mechanism other than the usual “username and password” and should be enabled wherever possible. They work by asking you for a code to confirm your login when accessing something; often an SMS or Email with a one-time code, but sometimes they ask you to use an app such as Google Authenticator to provide a short-lived code.
2FA and MFA will deny you access to that Legal Portal or your emails if you provide an incorrect code or none at all. Essentially, they confirm that it is really you trying to access something. They’re not entirely bullet-proof, but are another step to securing your online accounts.
Look out for email and text alerts; nowadays, many services will email you if a login has been detected on a device where the credentials haven’t been used before.

There are hardware MFA devices such as the ‘YubiKey’ that provide the same functionality as a time-based code MFA mechanism, where you have to insert a physical security device into your laptop to do this authentication step. Quite often, they will integrate biometric authentication – such as fingerprint access – to use them, adding that extra security factor.
5. Don’t share data you’re not authorised to share
Finally, don’t share information that you’re not supposed to. This might be one of the legal professional security tips that seems obvious but, astonishingly, it still happens!
Sharing confidential data exposes companies and individuals to GDPR violations that can result in prosecution or hefty fines. If someone internally asks for a spreadsheet of sensitive data, check with your Data Security team that you are permitted to do so. Ensure this is in writing and certainly don’t share internal data with external parties.
Securing data for transmission
Every legal business will vary, but generally there will be some kind of secure platform or cloud storage where data can be shared securely. Always ensure that where you’re storing the data has permissions locked-down where you grant access to individuals other than yourself where you need to.
Sharing sensitive data externally
Let’s say you’re a commercial solicitor and you need to share data with a client. Yet again, your business should have procedures in place for sharing this kind of data, but where it’s hosted should be encrypted and there should be some kind of gatekeeping mechanism in place, such as an area protected by a login and avoid sending sensitive data as an email attachment.
In summary
As a legal professional, you’ve got enough on your plate without cyber security or data security adding additional pressures. By following my legal professional security tips and using tools like Dracoeye, process, technology, common sense and services, you can ensure you operate in a way that won’t compromise your client data. This allows you to operate safely and with peace of mind. If you’re ever in doubt, speak to your internal IT or Data Security teams, who more often than not, will provide details on tools, services and policies in place already.
If you or your business needs to speak to us about how we can help you secure your legal business, please don’t hesitate to contact us.





